what it builds before it ships.
and scores risk in real time, so you ship fast without shipping vulnerabilities.
SOC2
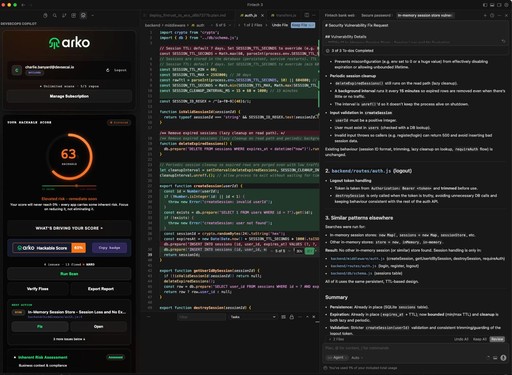
AI writes the code. ARKO decides if it ships based on the score.
AI copilots generate faster than humans can review. ARKO continuously analyses AI‑written code in real time, mapping risk to real attack paths – before it reaches production.
How It Works
DevSecOps Reasoning, not SAST or Rules Based.
ARKO watches AI-driven development happen - and quietly improves outcomes.
Invisible DevSecOps power at your side - improving every commit.
Faster, safer releases
ARKO identifies risk as code is written - not after it’s merged. Security issues are resolved earlier, so releases move faster without increasing exposure.
Shorter time to fix real risk
Developers see security feedback immediately, in the same place AI code is generated. No context switching. No security side-quests. Just faster resolution.
Coverage across AI systems by default
ARKO continuously observes applications, APIs, models and agents as they evolve - ensuring security coverage keeps pace with AI-driven change.
Lower MTTR on critical issues
Risk is prioritised based on real exploitability and business impact - so teams act on what actually matters first.
Compliance emerges naturally
Security decisions, controls and mitigations are captured as they happen - creating audit-ready evidence without extra work.
Clarity for security leadership
CISOs see whether AI-driven engineering is becoming safer over time - without relying on noisy tool metrics or manual reporting.